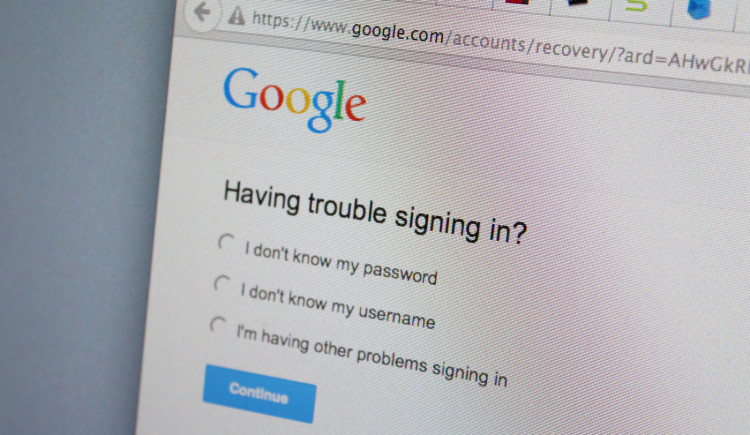
I had an interesting morning… You generally should not see this screen on your 6 month old iPhone while you are out and about doing errands…
9:30 AM
My wife visited me at work because her phone stopped working. It had shut down spontaneously, and she thought perhaps it was broken. It turns out it was more than just not working. It had been remotely erased via iCloud. Obviously, neither of us did it, so began the panic of figuring out who was in our account, how they breached our account, and how to get them out.
I tried logging into iCloud, but it would not accept the password. I initiated a password reset, only to find that the recovery email address, a Gmail account, was also not accepting the correct password. Great…
9:35 AM
Unfortunately, Gmail was the most difficult account to recover (and most time consuming). Gmail provides a means of recovering an account if someone other than the owner changes the password. Unfortunately it was very difficult to get all the information they wanted. Some of this information includes:
- Date that the email address was created
- Security question answers
- Frequent contacts (5)
- Oldest recovery email address
- Dates other Google services were registered
After trying about 10 times (with a lot of frustrated yelling…), I finally hit the combination of answers that let me back into the account. I changed the password, and began looking for evidence of damage.
The perpetrator did not enable forwarding. Well, that’s good. He did remove the recovery email address, and he also took the time to delete every email in the inbox and outbox.
10:00 AM
We checked other accounts tied to that email address. Our Amazon account password was changed, however nothing else appeared to be touched. No orders, no change of address, no change in credit card information, etc.
We called Amazon to see what to do in cases like this. I wanted them to verify that nothing was changed, and that no orders were placed. They in essence told us that they couldn’t do anything for two days, and to not use the account for the time being. It was fairly frustrating because it felt like they had no motivation or means for helping people in this situation.
10:30 AM
The rest of the day way spent changing passwords, and verifying that no other accounts were breached.
I filled out a request to Google to restore the deleted email messages thinking that they would be non-responsive, however, they kindly complied within 20 minutes or so. The restored emails show the time line of events, as well as give some closure as to what additional sites the perpetrator attempted to breach.
9:00 AM – There was an alert that the Gmail password reset had occurred.
9:05 AM – Notification of change of recovery email address.
9:11 AM – Notification of password reset for iCloud.
9:20 AM – Notification that the iPhone had been wiped.
So, clearly, the Gmail account was the weak link in this scenario. My guess is that the intruder guessed the security questions required to reset the password.
What is the Takeaway?
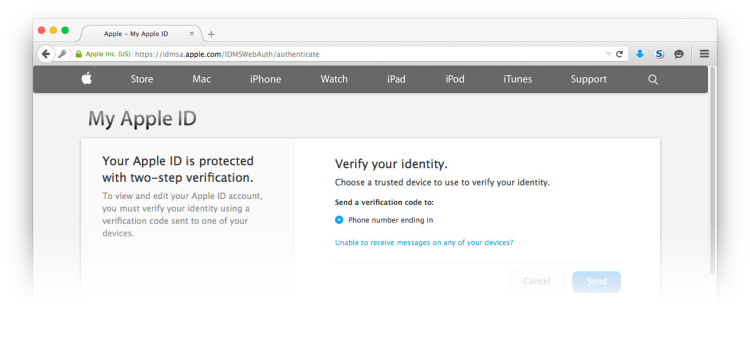 Although the intruder had decidedly ruined our day, nothing of consequence was hurt. No bank accounts were affected, and no fraudulent orders were made. Only a few family videos may have been lost from the iPhone.
Although the intruder had decidedly ruined our day, nothing of consequence was hurt. No bank accounts were affected, and no fraudulent orders were made. Only a few family videos may have been lost from the iPhone.
It appears that this was just someone being annoying rather than someone attempting to steal our identity, or money.
We have now upped our security by doing the following, and recommend that you do too:
- Utilize 2-factor authentication when it is available
(Gmail and iCloud both offer this) - Use longer/harder passwords
Relevant xkcd… - Use passwords that are unique for each site and application
If one service you use has a security breach, at least you don’t have to worry about any other accounts. - Do NOT use security questions if you can avoid it
If you have to use security questions, use obscure responses that are not easily guessable or contextually relevant.
All in all, things could have been a lot worse, and we are lucky we were able to get everything back under control so quickly. Still, it’s always better to practice good security before there is a problem